DVWA - Setup Burp Intruder
One of Burp Suite most powerful feature is the intruder. This feature allows us to set variables in a request and to iterate over values, replace the variables by the values and send a request for each variable.
With this feature we can fuzz an application or try to brute force some credentials.
In our example we will brute force some credentials.
Sending the request to the intruder
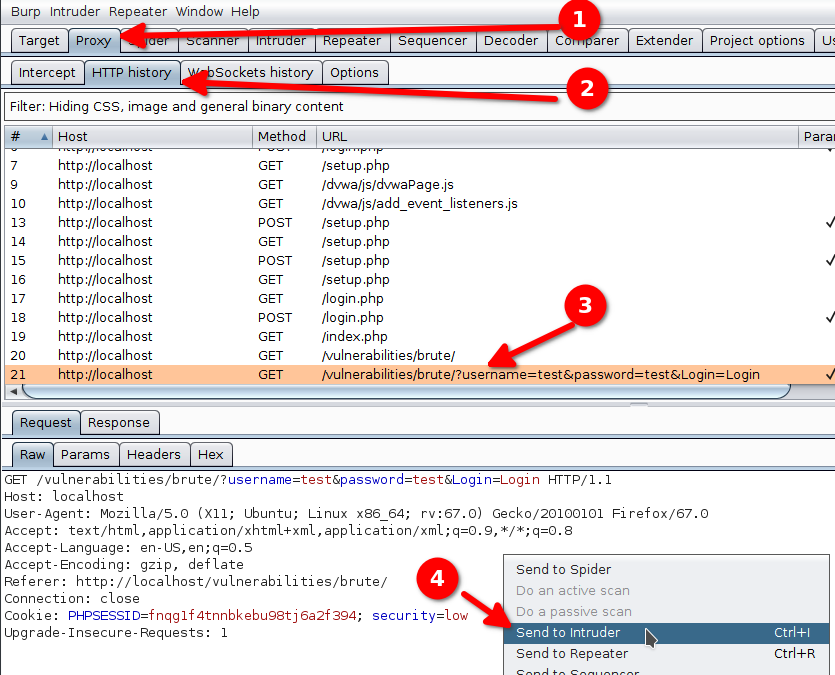
The first step to use the intruder is to get a request.
- We navigate to Proxy > HTTP history.
- We select the request we want to modify.
- We right-click on the request and select Send to intruder.
- We navigate to Intruder.
Configuring the variables
The first interesting tab of the intruder interface is the position tab. This tab lets us configure which part of the request will vary. Burp Suite offers an automatic detection of variables. In our case we are not interested and use §Clear§ to remove every variable.
A variable is a piece of text surrounded by the § character.
To add a variable we have two options :
- Add the
§character before and after the text that should vary. - Select the text that should be variable and click on §Add§.
We add the username and password as variables.
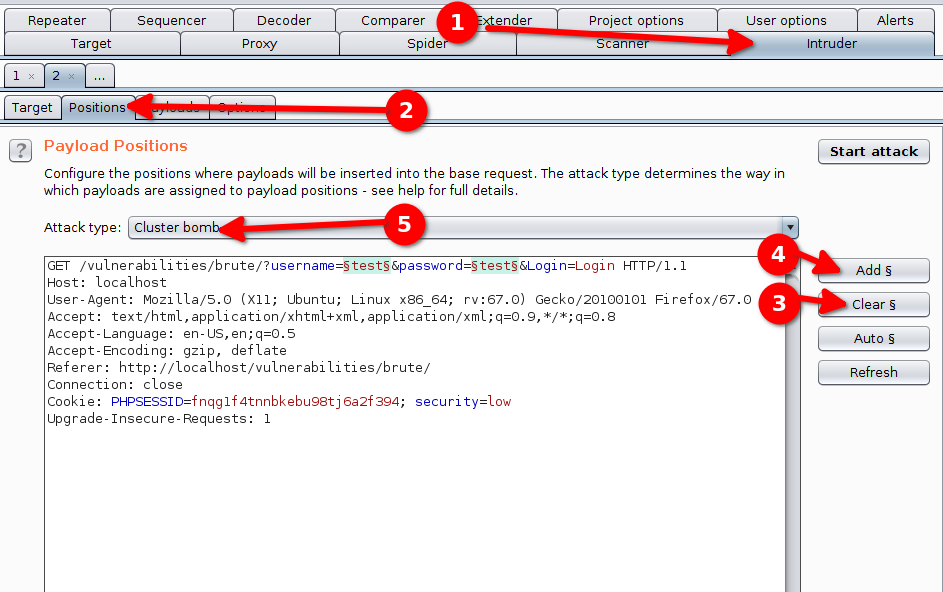
We also select the attack type : Cluster bomb.
Payloads
The Payloads tab configures the list of strings we want to try. Here we will start by configuring the list of usernames :
- Select the payload set 1 which corresponds to the first variable (username).
- Click Load and select the file containing the list of usernames to try.
- Click Open to load the file.
- The list is now loaded.
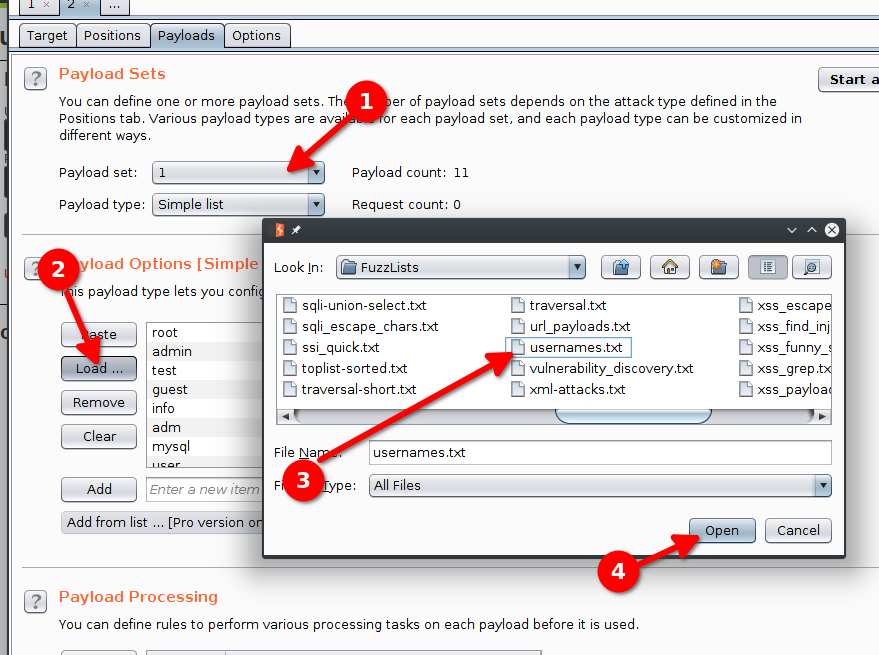
We have to repeat the operation for the list of passwords (we choose the paylaod set 2).
Options
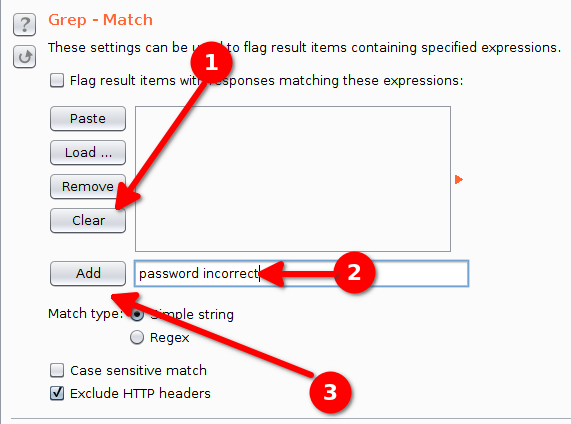
Our attack is completely configured now and we can start it with Start Attack if we want to. That being said, we would like to know when some credential stuffing worked. We use the Grep - Match option in the Options tab to detect successful login attempts.
We know that failed login attempts will trigger a response containing the words “password incorrect”, so we configure the tool to add a flag to a response with these words :
- Click on Clear to remove existing filters.
- Enter the new item “password incorrect”.
- Click Add to add the new item.
Now we can start the attack.
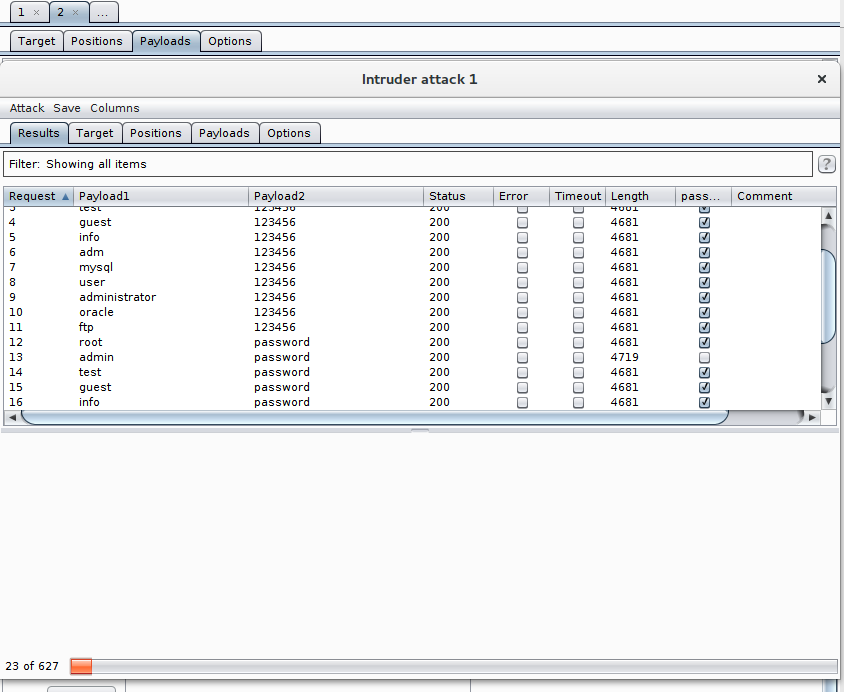
Results
The results are presented in a table. We can select the responses that are not flagged with our grep configuration to detect successful login attempts.