DVWA - Start with Docker
In this series of posts I will detail my personal solutions to the Damn Vulnerable Web Application challenges.
In this particular post I will explain how I start the vulnerable application with Docker.
Recaptcha keys
The Recaptcha challenge needs us to have a reCAPTCHA key. We can get one for free from Google if we have a Google account.
Simply follow the steps from the official Google page.
A good tutorial is also given here.
The domain will be localhost as DVWA will be run on your machine.
Docker installation
First of all, we need Docker installed for our setup to work properly.
We can follow the official documentation to install it on Ubuntu.
DVWA image
Once Docker is installed and working, we need to retrieve the source code used to create our DVWA image.
We clone opsxcq’s repository with the following command :
git clone https://github.com/opsxcq/docker-vulnerable-dvwa.git
We modify the Dockerfile to add the line COPY php.ini /etc/php/7.0/apache2/php.ini.
COPY php.ini /etc/php5/apache2/php.ini
COPY php.ini /etc/php/7.0/apache2/php.ini
COPY dvwa /var/www/html
We then modify the file config.inc.php to add our Google reCAPTCHA keys generated previously.
vim docker-vulnerable-dvwa/config.inc.php
# ReCAPTCHA settings
# Used for the 'Insecure CAPTCHA' module
# You'll need to generate your own keys at: https://www.google.com/recaptcha/admin/create
$_DVWA[ 'recaptcha_public_key' ] = 'example_public_key';
$_DVWA[ 'recaptcha_private_key' ] = 'example_private_key';Now that our key is configured, we can create our Docker image with the name dvwa :
cd docker-vulnerable-dvwa
docker build -t dvwa .
Starting DVWA
To start DVWA we use the command :
docker run --rm -it -d -p 80:80 dvwa
f948a51fc0a758c6104bc4e1f8fa2dc1a0a0be25a30badb1075ac742c3b2ed33
Docker will give the newly created container an id used to reference the container when using commands such as stop and rm.
We used the option --rm when starting the container. Because of this, the container will automatically be removed when stopped.
We can access the vulnerable application through the following URL : http://localhost.
The id and password are admin and password.

We click on Create / Reset Database to initialize the database. You can safely ignore the warning about the allow_url_include misconfiguration, this is a bug.
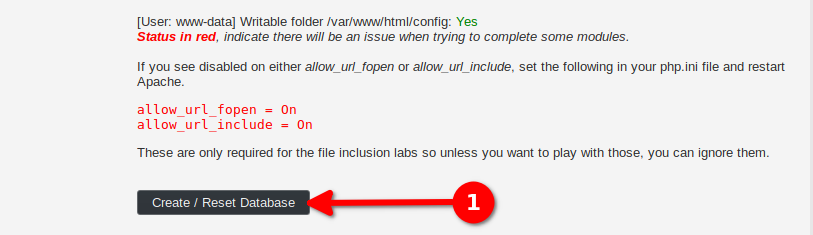
We are then redirected to the login page, use the same credentials as before.
You can now use the left menu to access the challenges.
Setting the difficulty
There are four levels of difficulty in DVWA :
- low
- medium
- high
- impossible
Use the menu DVWA Security to set the levels of difficulty.
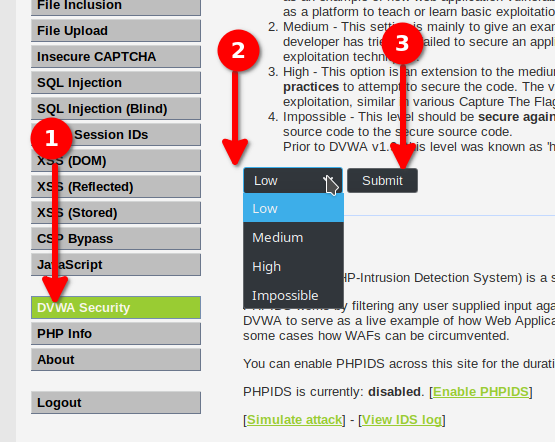
You are now set up and can try breaking the application.
Stopping the container
To stop the container, get its id with docker ps :
docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
f948a51fc0a7 dvwa "/main.sh" 12 minutes ago Up 12 minutes 0.0.0.0:80->80/tcp goofy_feistel
You can then user docker stop f948 to stop the container.